Data privacy is a big thing in Germany. Really big. For instance, Germans guard their PIN numbers with utmost ferocity, hunching over the keypad to such a degree that it’s a wonder that there’s even enough light to see which keys they’re actually pressing. However, in addition to being a repetitive redundancy, PIN numbers are actually extremely useless without mugging the person and taking away their bank card. (Which is something that I’ve actually told people who berate me for being “too close” when they are trying desperately to find the right numbers on the keypad.)
In fact, there are so many other possible examples of this degree of data-privacy paranoia, that you can almost be forgiven for thinking that the G in GDPR somehow stands for German …

But, trust the University here in Not-Bielefeld to ramp this whole issue up to the absurd. It’s not that data privacy is a bad thing, but more how the University is forcing it upon us, often to ridiculous extremes and extreme inconvenience. Their first action to once again save us from ourselves was when the use of Doodle was frowned upon some years back, with the Google Docs Editors suite finding its way into the crosshairs soon thereafter. Dropbox was also dropped somewhere along the way. Finally, enter the pandemic and exit video-conferencing tools like zoom or Skype. You’d almost swear that the University had something against the colour blue.
The official justification given for all this was data security: any personal data would not be going through any uncontrolled third-party servers subject to who knows what legislation, but would instead be hosted on the much more secure university servers via properly vetted software.
(I wouldn’t be surprised if the IT people at the University of Duisburg-Essen were thinking along the same lines right up until the cyberattack in November 2022 that utterly crippled the university’s entire IT infrastructure for months on end. You also have to remember that we’re talking about a university here where the entire printer network was hacked from the outside to spit out pages upon pages of nonsense. Whatever …)
In any case, we weren’t left completely hanging. Doodle became the very creatively named Stoodle, Google Docs and Dropbox became Nextcloud, and zoom & Co. became Big Blue Button. (Ok, so much for my conspiracy theory about the University hating the colour blue …) Unfortunately, in giving up those dreaded third-party servers, we’ve taken on mostly third-rate software. Whether you love or hate Google Docs, you have to admit that it works. Really, really well. Same for zoom. Big Blue Button and the secure university servers were simply not up to the task of hosting all the online teaching in the first wave of the pandemic. Some 18 months, a few updates, and a few waves later and it’s still touch-and-go. At a recent video conference in the University, it was recommended that only the moderator have their camera turned on so as to not bog down the system. You don’t hear this about zoom very often, now do you?
And, more to the point, I don’t hear all this happenning with any other universities. I’ve done my fair share of video conferencing in the past 18 months with more than a fair share of software (zoom, Skype, Microsoft Teams, Cisco Webex, …), but our university is the only one that I know of using something like Big Blue Button. And my collaborators from far and abroad are still happily sending me their Google Docs and Dropbox links.
Nevertheless, this is only the beginning. The silliness goes on …
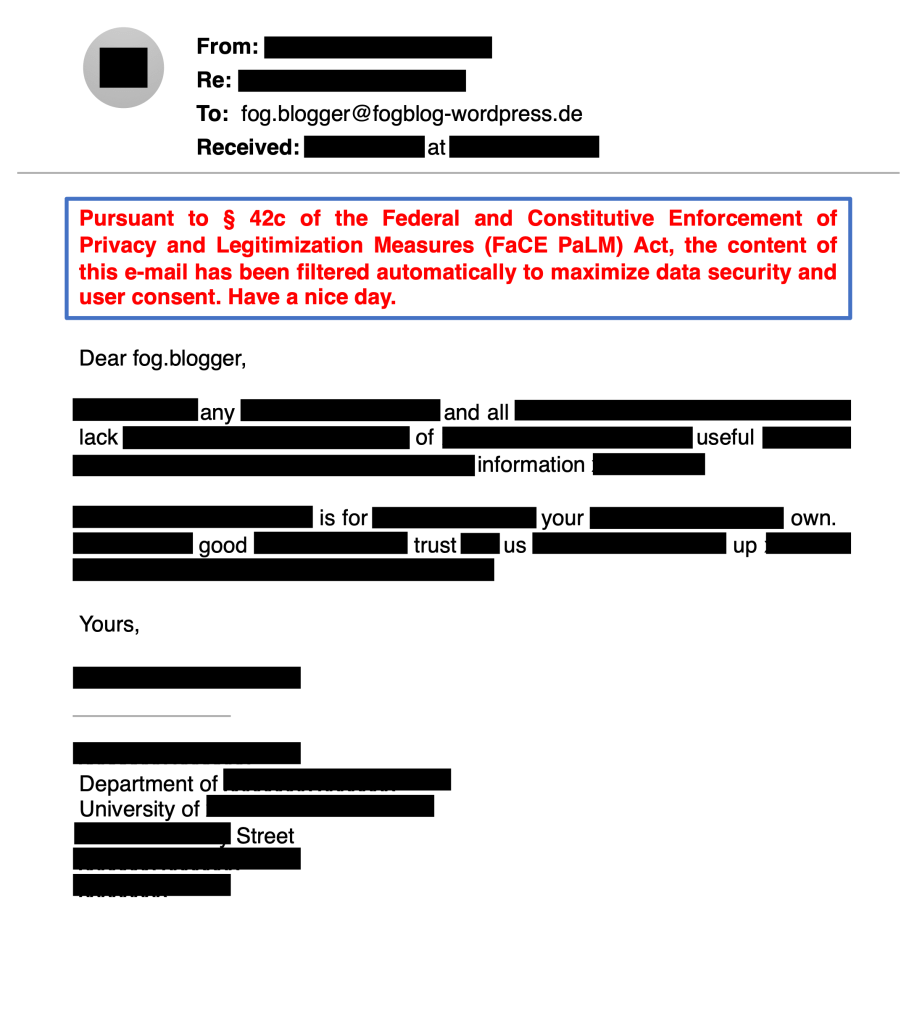
As I found out a few days ago, we’re also not allowed to forward our work-related e-mails to any private, third-party e-mail address that we might have. Apparently, this is because of a lack of consent on the part of the sender to having their e-mail processed by anything other than the university’s servers.
What kind of sheer, unmitigated nonsense is this? (And will anyone dare to admit to having thought it up? (Sadly, the answer to that last question is probably “yes”.))
For pretty much every e-mail that I’ve ever sent, my only expectation in doing so was that it reaches the person that it was intended for. I never for the life of me realized that I was consenting to anything on top of that. (Consentual e-mailing. What a concept. And a pretty forgettable one at that, especially for the spammers …) The whole situation actually becomes really, really terrifying when I now think about just how many third-party servers all those e-mails went through to reach these people, all without my consent! (Just check all the hidden headers on any external e-mail you get and you’ll see what I mean.)
This whole line of argumentation is akin to saying that I can’t take a letter (remember those?) out of my mailbox because someone else might see it. In fact, if you follow the, ahem, logic underlying this consent argument, it would also mean that you can’t print out any work-related e-mails. (Definitely a no-go at home for my University.) Even worse: all the e-mails that I receive exist for only fractions of a second on the university servers before they are downloaded to my third-party laptop. Even if it’s an Apple laptop (or perhaps because of it because our IT department is lost if it ain’t a PC), that must be illegal too and yet another good reason to keep this blog anonymous.
More to the point: how much of all this information is actually useful, or indeed even vaguely interesting, to anyone else? What is some data pirate going to do with the knowledge that our annual Christmas party will take place on the 20th starting from 4 PM and that Jimmy, Sally, and Susie can’t make it? Hell, come and crash it for all I care. There’s three empty places after all.
But, I could be wrong here …
There was recently a successful phishing expedition at the University where a considerable number of people—despite explicit, incredibly gaudy warning labels attached to every external e-mail that are impossible to overlook—gave hackers all their login details. In fact, it apparently was considerable enough that the University forced everyone to reset their passwords to prevent the hackers from, and I quote, “gaining access to the scientific knowledge of the University”.
Scientific knowledge?
Looks folks, most hackers are not of the industrial-espionage sort and looking to steal our valuable data so as to publish them before we can. (If they are, again, go ahead for all I care. Let them deal with all the idiotic comments and brain-dead suggestions of that damn third reviewer. (Which, in this case, might turn out to be me come to think about it.)) For most of the University (and I readily include myself in that most), we’re not really talking about NASA, the Pentagon, or even Coca-Cola levels of research here. What state secrets can someone, say, in the Music Department possibly be hiding? A new note?
And for that small percentage of the University where we really might be talking about “for your eyes only” knowledge, you do have to wonder just how good it can possibly be coming from someone whose eyes missed a phishing attack with all the bells, whistles, and gaudy labels attached to it …


